Prime numbers are the positive whole numbers having just two components, 1 and the whole number itself. For instance, components of 6 are 1,2,3, and 6, which are four variables altogether. Yet, components of 7 are just 1 and 7, absolutely two. Thus, 7 is a prime number however 6 isn’t, rather it is a composite number. However, it is important to know that 1 is neither a prime nor a composite number.
We can likewise say that the prime numbers are the numbers, that are divisible by 1 or the number itself.

Encryption in cryptography is the method of encoding data. This method converts the original representation of the data, known as plaintext, into an elective structure known as ciphertext. Preferably, only approved parties can analyze a ciphertext back to plaintext and access the original information. Encryption doesn’t forestall interference yet denies the comprehensible content to an eventual interceptor.
The three significant encryption types are AES, DES, and RSA. While there are numerous kinds of encryption. The vast majority of the others are different from older ones, and some are not, at this point recommended or supported. Tech is advancing each day and even those viewed as modern will be replaced by newer versions eventually.
DES encryption is not, at this point known to be safe on its own. It encrypts only 56-bits of information at a time and it was discovered to be effectively hacked not long after its introduction. Advanced Encryption Standard (AES) is the most secured type of encryption. It utilizes “symmetric” key encryption. Somebody on the receiving end of the information will require a key to decode it. However, this article is mostly centered on RSA encryption.
RSA Encryption
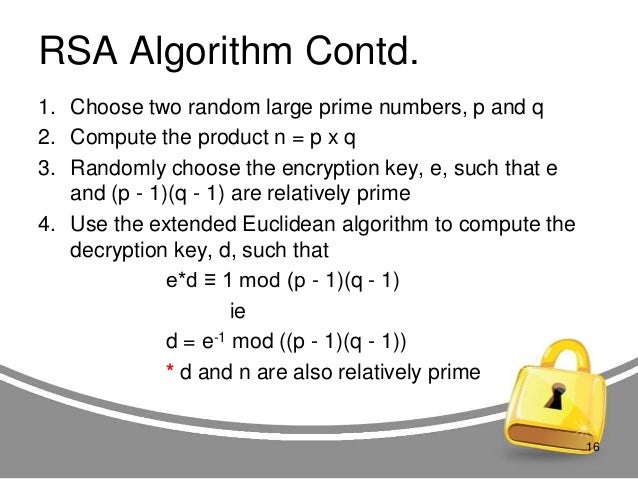
Another well-known encryption standard is “Rivest-Shamir-Adleman” or RSA. It is generally utilized for information sent on the web and depends on a public key to encrypt the information. Those on the receiving end of the information will have a private key of their own to decode the messages.
It’s proven to be a safe method to send data between individuals who may not have a clue about one another and need to communicate without compromising their sensitive or personal information.
The RSA encryption system utilizes prime numbers to encrypt information. The purpose behind this is a direct result of how hard or difficult it is to locate the prime factorization. This system, which was created by Leonard Adleman, Ron Rivest, and Adi Shamir, secures the transmission of information such as credit card numbers on the web.
Source: Slideshare.net
More explicitly, RSA fundamentally relies upon the knowledge that prime factorization of huge numbers takes quite a while. Basically, there is a “public key” comprising of a product of two enormous primes used to encrypt a message, and a “secret key” comprising of those two primes utilized to decrypt the message.
An RSA user makes and publishes the result of two huge prime numbers, alongside an auxiliary value, as their public key. It is important that the prime factors are kept a secret. Anybody can utilize the public key to encrypt a message, however with currently published techniques, if the public key is adequately huge, it is only somebody with information on the prime factors that can practically decode the message.
Fields Utilizing RSA for Security Reason
E-Commerce:
The RSA Algorithm is regularly utilized for making sure communications between internet browsers and eCommerce sites are secured. The explanation behind this is the protection from attack. It is likewise surely known as several researchers have studied for years. The connection utilizes a secure socket layer (SSL) certificate, which is made from people in private and public keys. The subsequent pseudo-irregular number forms the reason for the certificate, which is introduced at each end of the connection to guarantee secured communications.

Source: rsa.com
Financial Institutions
In India, many financial institutions have set up additional security steps for access to virtual banking, but there is no consistency in the approach adopted. Internet security threats are not too risky when we follow the right steps to make our computers and connections secure. To solve most of the security-related concerns in virtual banking, RSA is used in some form or the other. This paper appraises the performance of RSA in virtual banking.
As banking institutions offer more transactions and services online, security becomes required. Security problems in virtual banking regularly comprise inquiries of obtaining globally acknowledged minimum technology standards for firewalls, access control, digital certificates, minimum key length utilized in the encryption algorithms, signatures, and so on.
In India, numerous financial institutions have set up extra security ventures for access to virtual banking, yet there is no consistency in the methodology embraced. Internet security dangers are not all that risky when we follow the correct steps to make our PCs and connections secure. To solve the greater part of the security-related worries in virtual banking, RSA is utilized in some form or the other.
Government Officials
Federal, state, and local governments and defense and intelligence agencies are progressing computerized transformation to all the more likely serve constituents, secure the country, engage and connect citizens, and increment organization proficiency in a quest for their missions. These developments take advantage of strong technologies that are enabling individuals and communities to flourish in a thriving, digitally connected world.
Reference:
- https://store.hp.com/us/en/tech-takes/what-are-different-types-of-encryption
- https://www.splashlearn.com/math-vocabulary/algebra/prime-number
- https://en.m.wikipedia.org/wiki/Encryption
- https://randerson112358.medium.com/prime-numbers-and-cybersecurity-9a440eb39229














